NSA's Hacking Tool and Wannacry Ransomware
The world awoke today to the largest cyber security threat ever, with a ransomware wannacry holding hundreds of thousands computers hostage. More than 100 countries are infected by the ransomware, with the users locked out of their vital files and data. The criminal group behind the ransomware is asking for $300 in bitcoin, for releasing the files they back to their users. Reports indicate that the bitcoin purse is filling up, as people desperate for getting control of their machines, are paying up.
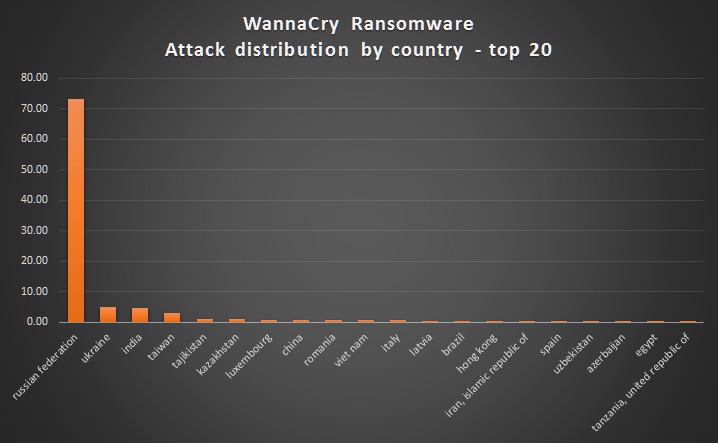
According to Kaspersky Labs, one of the major security firms in the world, India had the third highest number of infected machines, with only Russia and Ukraine being worst hit. A number of hospitals in the UK, telephone systems in Spain and Italy have been hard hit.
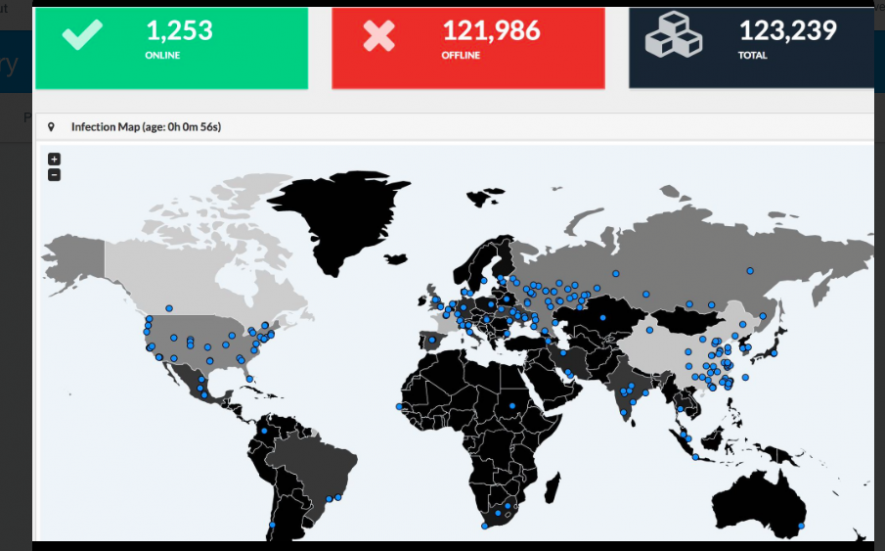
Infection Map of Wannacry
How did this happen? In April this year, a group called Shadow Brokers dumped online NSA's cache of cyber weapons/hacking tools. NSA's tools can hide inside machines and transmit information back to NSA, or take control of the machines themselves. These were one of the most sophisticated set of cyber weapons that security experts had ever seen. The security experts had then pointed out that NSA had either found a large number of backdoors in existing software from companies such as Microsoft, Apple, etc., or such backdoors were being deliberately provided by the companies themselves to help the NSA in its hacking.
In this particular case, Microsoft Window's vulnerability was exploited by the criminal group behind wannacry ransomware. Using a particular NSA hacking tool called EternalBlue, the group created a worm that could spread from machine to machine, infecting them. Once infected, the ransomware encrypted the original files of the machines, and deleting the original files. While installing security patches to Windows can protect the machines from future infections, decrypting the encrypted files is not easy without paying the ransom. Alternatively, the users can forget about these files, format their machines, reinstall all the software, and load the back-ups.
Luckily for the world, the ransomware had a kill switch disguised as a domain name. Once the UK security expert, who saw this code, bought the domain, it started to receive thousands of connections from infected machines. It appears that once the domain is found to be live, it acts to stop all further spread of the worm. It appears that the spread of the infections have now slowed down, possibly because of this kill switch now becoming active.
The current infection route of wannacry uses an old security hole in the MS Windows operating system that seems to have been present from Windows XP days. Microsoft does not support Windows XP anymore, meaning that though it does release patches for its current generation of operating systems, no such patch exists for systems running Windows XP. "The bad news is that new versions of WannaCry have been released after the announcement of the kill-switch, which are now unaffected by it."
In March this year, Microsoft had released a security patch blocking this particular hole, and therefore infections using EternalBlue. The global agencies have been giving a slant to the news regarding wannacry that the users are at fault, as they do not upgrade their system software regularly. The far more important question is left unasked, why did Microsoft take more than 5 years to provide a patch for this security hole?
The security hole was being used by NSA for years to “capture” target systems. Did NSA not inform Microsoft of this hole, as it wanted to keep its ability to hack into such target Windows machines? Or was their collusion between NSA and Microsoft to create and maintain this hole?
Ars Technica reported Microsoft's suspicious fix of four zero-date (security holes not known previously) fixes exactly a month before the Shadow Brokers NSA tools dump. It wrote, “Those updates – which Microsoft indexes as MS17-010, CVE-2017-0146, and CVE-2017-0147 – make no mention of the person or group who reported the vulnerabilities to Microsoft. The lack of credit isn't unprecedented, but it's uncommon, and it's generating speculation that the reporters were tied to the NSA.”
NSA was well aware for some time that its cyber weapons cache had been hacked. Did the NSA inform Microsoft of its loss, leading Microsoft to hurriedly releasing this security patch?
This huge threat to computer systems worldwide, raises the important question that if security agencies create cyber weapons, what kind of risk does it pose for all of us? The dump of NSA's cyber weapons had raised serious concerns from the security community as their toolkit was far beyond what any criminal group could create, it posed enormous risks to the computer systems that pretty much run everything today. NSA's tools were not only superior, but as they worked with the US companies, they could also exploit backdoors purposely created for them. The problem is that any such backdoor either left open inadvertently or wilfully created by the system developers, has a good chance of being found by hackers as well. That is why the demand for a cyber weapon ban and the importance of treating the internet as a non-weaponised space, the same way as outer space.
Disclaimer: The views expressed here are the author's personal views, and do not necessarily represent the views of Newsclick
Get the latest reports & analysis with people's perspective on Protests, movements & deep analytical videos, discussions of the current affairs in your Telegram app. Subscribe to NewsClick's Telegram channel & get Real-Time updates on stories, as they get published on our website.
























