What Is Ravishankar Prasad Hiding on WhatsApp Hack?

As many as 1,400 worldwide smartphone users—including 140 Indians—have been hacked. This hack used Pegasus, a software toolkit from the notorious hacker-for-hire, the Israeli company NSO or Q Cyber Technologies. The fundamental question for us is: whodunit? A simple question that the government refuses to answer.
Political parties and others are asking if an Indian government agency bought Pegasus from the Israeli company and used it against its own citizens. Are we, as Justice Srikrishna said, becoming an Orwellian surveillance state? Justice Srikrishna headed the committee that gave detailed recommendations on framing a data and privacy protection law. Its recommendations were submitted in 2018, but the government has dragged its feet in bringing a law to protect the privacy of citizens.
If we listen to Electronics and Information Technology Minister Ravi Shankar Prasad, all of this is either the fault of the Congress party, which used to bug their opponents phones, or Facebook’s fault. He has asked WhatsApp to “explain” the hacks. In other words, he is deflecting from the simple and straightforward question: did a central government agency buy or license hacking tools from the Israeli company?
According to rules notified in 2018 under the Information Technology Act, ten central government agencies have the power to intercept communications. Yet the Home Ministry has refused a clear answer to an RTI request asking if the agencies under the Home Ministry had procured Pegasus. And what about agencies such as the NTRO [National Technical Research Organisation], RAW [Research and Analysis Wing] and the CBI [Central Bureau of Investigation], which are not administratively under the Home Ministry?
Why is the voluble Ravi Shankar Prasad, who otherwise offers his opinion on everything under the sun, so coy about providing a straight answer to this question? The Communist Party of India (Marxist) issued a press statement on 2 November, which says that the government “needs to answer whether any of its agencies were involved in the use of this hacking software, particularly since most of the persons affected were targeted by the government in May last year. Under law, hacking peoples phones would constitute a cyber crime. If the government is not involved in the Pegasus software as it claims, why has it not filed a FIR and started criminal investigations?”
NSO, the Israeli company, has claimed that it supplies such software only to government agencies. If indeed Indian government agencies are not involved, then the hacking of smartphones constitutes a criminal offence in India. Why has the government, specifically the IT Ministry, not filed a police complaint and launched criminal investigations?
The only legal step taken in this hacking incident is by Facebook, which owns the WhatsApp platform. It has filed a civil suit claiming damages against NSO and Q Cyber in a Federal Court in San Francisco, United States (US).
Blaming the Congress for previous misdeeds, including the Emergency, does not absolve this government from performing its constitutional duties. Or is the IT Minister really convinced by his own kindergarten-level alibi that “the Congress did it first”?
NSO is notorious for supplying hacking tools to governments and spy agencies. Among its 45 buyers are countries including Saudi Arabia and the United Arab Emirates, who have used its tools to hack phones and computers of their critics. It was widely reported that Saudi dissident Jamal Khashoggi’s iPhone was hacked by his country’s intelligence agencies using Pegasus, before his killing at the Saudi’s Istanbul consulate.
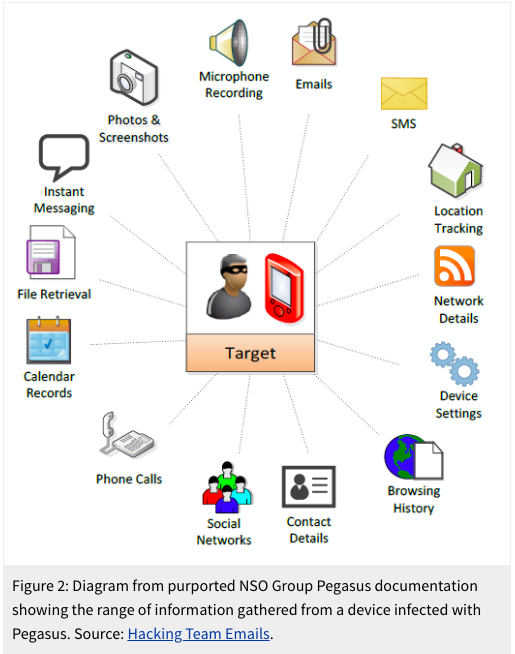
What is Pegasus’ “software” and how does it affect smartphone, particularly WhatsApp, users? The Israeli company supplies hacking tools for various kinds of devices including iPhones and Android-based phones, which have a near 100% duopoly over the smartphone market. The hacking is particularly embarrassing for WhatsApp, which has been publicising its 100% end-to-end encryption widely. They neglected to tell their users that such encryption does not help if the user’s phone is hacked. (WhatsApp information is available, unencrypted, on phones.)
What compounds their humiliation is that the Pegasus hacking software exploited a security hole in WhatsApp’s software.
(From The Citizen Lab Report HIDE AND SEEK, September 18, 2018)
This security hole has been patched by WhatsApp, but only this one hole. Many others are not even known of yet. Such still-unknown holes, which are called zero-day exploits, are unknown to even the supplier of software. They are sold on the Darknet by criminals. Companies pay big money to hackers—often the same criminals who inhabit the Darknet—to discover these security gaps.
If the buying and selling of such software were limited to just the criminals or companies intent on patching vulnerabilities, the problem would have been far smaller. In fact, government intelligence agencies’ have entered this business and worsened the situation, for they bring in big bucks and large teams to tap into leading research institutions—all in the name of national security.
While the US and western media have been talking about Russia and China, they are largely silent on Israeli agencies and, of course, the US agencies NSA-CIA, and the United Kingdom’s GCHQ. These three intelligence agencies have developed the most extensive suites of software or attack tools to penetrate computers, smartphones and the switches and routers that are a part of the telecom infrastructure of every country and even every home.
In this sense, hacking tools and cyber weapons are not significantly different, only their purposes vary. If anybody hacks into a computer or a phone, the hacker—and not the consumer—effectively owns the phone. They can control what the device does.
Domestic laws in the US, permissive as they are under their so-called Global War on Terror, still have a modicum of protection on domestic surveillance; even under the FISA or Foreign Intelligence Surveillance Courts, which give American security agencies a very wide latitude.
We know from the revelations of Snowden and WikiLeaks that the US had penetrated the telecom infrastructure of every country and had a backdoor to US-manufactured equipment and software platforms through which it could install spyware.
Israeli agencies work closely with the US agencies. The US cannot sell such weapons-grade cyber software or equipment to “friendly” monarchies and fascist rulers as they are barred by export-control rules. In the US, such software is recognised as a weapon, and their exports are strictly controlled. There are no such controls for the Israelis, who use a number of companies that are very closely tied to its military and spy agencies.
NSO and other such companies are essentially a US-Israeli arm: supplying software tools to spy agencies of “friendly” governments. Selling such software tools to governments provides the US and Israel with additional intelligence feeds. Countries, including India, may feel that they have “bought” this software, but it runs on “servers” that have been set up by companies which, once again, are linked to the Israel government.
All information gathered by such software is routed to Israel and American spy agencies. When governments buy this software from foreign sources they are, in effect, partnering with foreign agencies to spy on their own citizens. They are helping foreign powers shape the domestic narrative. If NTRO or RAW have indeed bought Pegasus, the narrative that such hacking can produce can be easily manipulated by Israeli or US spy agencies.
This is the risk of “outsourcing” intelligence operations and tools. As a Reuters report on the victims of the WhatsApp Pegasus breach says, “...a ‘significant’ portion of the known victims are high-profile government and military officials spread across at least 20 countries on five continents. If the NSO’s claims of selling only to governments are correct, either the Pegasus spyware was used by governments to hack each other, or they were victims of Israeli spying.
To compound the danger, in 2017, NSA and CIA spyware tools were dumped by hackers on the net, where criminals can readily exploit them. This shows how dangerous such software is for everybody, not just activists. Such tools are particularly perilious for they are not the handiwork of merely a few hackers but have the resources of a state behind them.
In short, these are not hacking tools but cyber weapons. That is why governments need to sign a moratorium against developing and deploying them, just as they have for chemical and biological weapons.
Get the latest reports & analysis with people's perspective on Protests, movements & deep analytical videos, discussions of the current affairs in your Telegram app. Subscribe to NewsClick's Telegram channel & get Real-Time updates on stories, as they get published on our website.
























